Which security principle requires more than one person is required to perform a critical task?
A.
least privilege
B.
need to know
C.
separation of duties
D.
due diligence
separation of duties
Which incidence response step includes identifying all hosts affected by an attack'?
A.
post-incident activity
B.
detection and analysis
C.
containment eradication and recovery
D.
preparation
post-incident activity
A malicious file has been identified in a sandbox analysis tool.
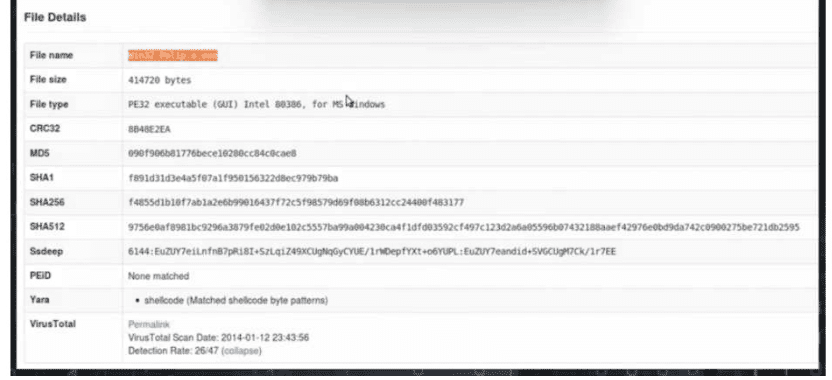
A. file header type
B.
file size
C.
file name
D.
file hash value
file hash value
What is the difference between deep packet inspection and stateful inspection?
A.
Deep packet inspection is more secure than stateful inspection on Layer 4
B.
Stateful inspection verifies contents at Layer 4 and deep packet inspection verifies connection at Layer 7
C.
Stateful inspection is more secure than deep packet inspection on Layer 7
D.
Deep packet inspection allows visibility on Layer 7 and stateful inspection allows visibility on Layer 4
Deep packet inspection allows visibility on Layer 7 and stateful inspection allows visibility on Layer 4
Refer to the exhibit.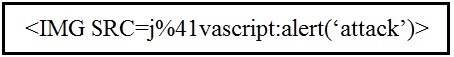
Which kind of attack method is depicted in this string?
A.
cross-site scripting
B.
man-in-the-middle
C.
SQL injection
D.
denial of service
cross-site scripting
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
A.
syslog messages
B.
full packet capture
C.
NetFlow
D.
firewall event logs
NetFlow
Refer to the exhibit.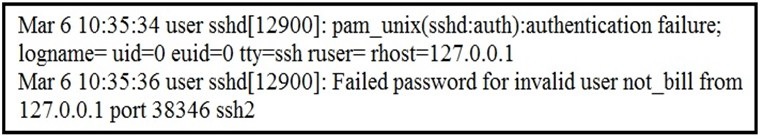
In which Linux log file is this output found?
A.
/var/log/authorization.log
B.
/var/log/dmesg
C.
var/log/var.log
D.
/var/log/auth.log
/var/log/auth.log
Which two components reduce the attack surface on an endpoint? (Choose two.)
A.
secure boot
B.
load balancing
C.
increased audit log levels
D.
restricting USB ports
E.
full packet captures at the endpoint
secure boot
restricting USB ports
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
A.
queries Linux devices that have Microsoft Services for Linux installed
B.
deploys Windows Operating Systems in an automated fashion
C.
is an efficient tool for working with Active Directory
D.
has a Common Information Model, which describes installed hardware and software
has a Common Information Model, which describes installed hardware and software
An analyst is investigating an incident in a SOC environment.
Which method is used to identify a session from a group of logs?
A.
sequence numbers
B.
IP identifier
C.
5-tuple
D.
timestamps
5-tuple
| Page 2 out of 41 Pages |
| Previous |