What specific type of analysis is assigning values to the scenario to see expected
outcomes?
A.
deterministic
B.
exploratory
C.
probabilistic
D.
descriptive
deterministic
Which category relates to improper use or disclosure of PII data?
A.
legal
B.
compliance
C.
regulated
D.
contractual
regulated
Which type of data collection requires the largest amount of storage space?
A.
alert data
B.
transaction data
C.
session data
D.
full packet capture
full packet capture
Which action prevents buffer overflow attacks?
A.
variable randomization
B.
using web based applications
C.
input sanitization
D.
using a Linux operating system
input sanitization
Refer to the exhibit
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been
downloaded from an email. What is the state of this file?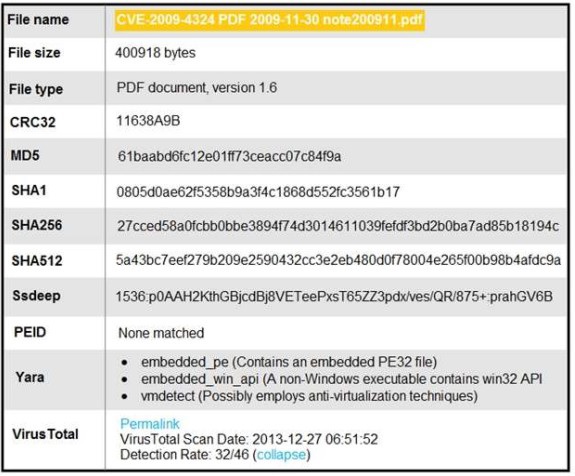
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
|
The file has an embedded non-Windows executable but no suspicious features are identified file has an embedded Windows 32 executable and the Yara field lists suspicious The file has an embedded executable and was matched by PEiD threat signatures for further analysis. The file was matched by PEiD threat signatures but no suspicious features are identified since the signature list is up to date |
|
file has an embedded Windows 32 executable and the Yara field lists suspicious
features for further
analysis.
How does an attacker observe network traffic exchanged between two users?
A.
port scanning
B.
man-in-the-middle
C.
command injection
D.
denial of service
man-in-the-middle
What makes HTTPS traffic difficult to monitor?
A.
SSL interception
B.
packet header size
C.
Cs
D.
encryption
encryption
Refer to the exhibit.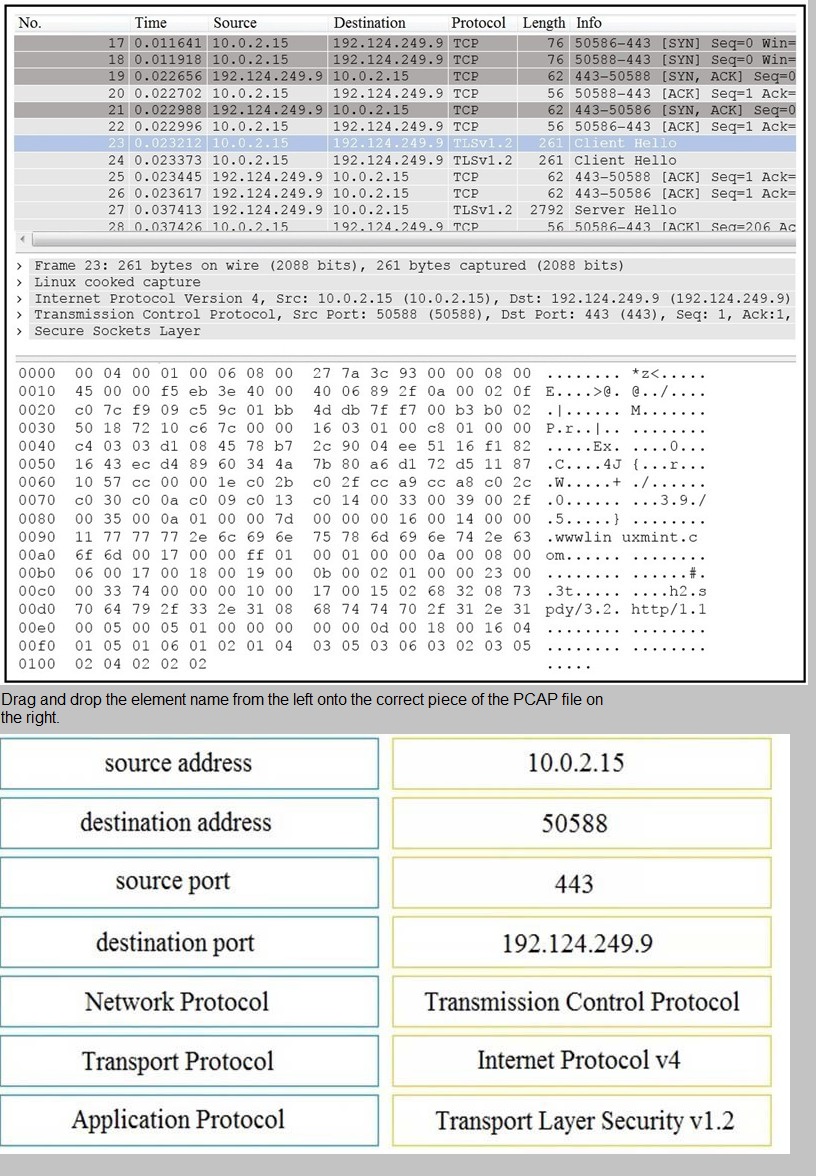
Which regex matches only on all lowercase letters?
A.
[az]+
B.
[^az]+
C.
az+
D.
a*z+
[az]+
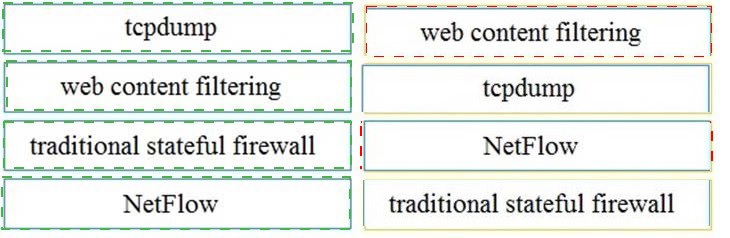
Drag and drop the technology on the left onto the data type the technology provides on the right.
| Page 8 out of 41 Pages |
| Previous |