At which layer is deep packet inspection investigated on a firewall?
A.
internet
B.
transport
C.
application
D.
data link
application
A security engineer deploys an enterprise-wide host/endpoint technology for all of the
company's corporate PCs. Management requests the engineer to block a selected set of
applications on all PCs.
Which technology should be used to accomplish this task?
A.
application whitelisting/blacklisting
B.
network NGFW
C.
host-based IDS
D.
antivirus/antispyware software
application whitelisting/blacklisting
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
A.
ransomware communicating after infection
B.
users downloading copyrighted content
C.
data exfiltration
D.
user circumvention of the firewall
user circumvention of the firewall
Refer to the exhibit.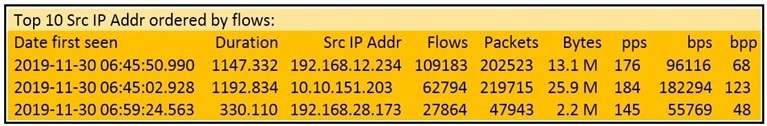
What information is depicted?
A.
IIS data
B.
NetFlow data
C.
network discovery event
D.
IPS event data
NetFlow data
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication.
Which obfuscation technique is the attacker using?
A.
Base64 encoding
B.
transport layer security encryption
C.
SHA-256 hashing
D.
ROT13 encryption
transport layer security encryption
Which event artifact is used to identify HTTP GET requests for a specific file?
A.
destination IP address
B.
URI
C.
HTTP status code
D.
TCP ACK
URI
Refer to the exhibit.
Which application protocol is in this PCAP file?
A.
SSH
B.
TCP
C.
TLS
D.
HTTP
TCP
Refer to the exhibit.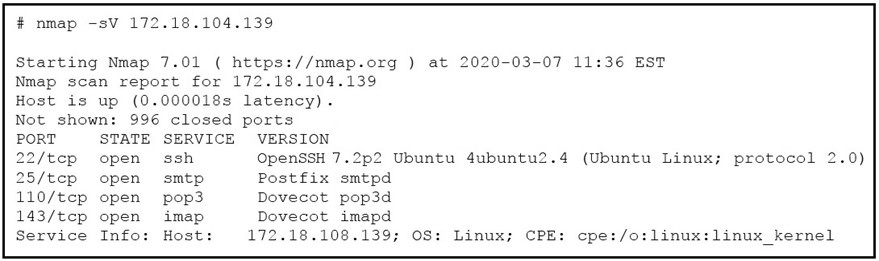 What does the output indicate about the server with the IP address 172.18.104.139?
What does the output indicate about the server with the IP address 172.18.104.139?
A.
open ports of a web server
B.
open port of an FTP server
C.
open ports of an email server
D.
running processes of the server
open ports of an email server
Refer to the exhibit.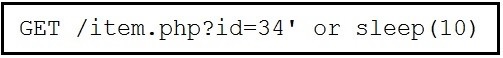
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
A.
parameter manipulation
B.
heap memory corruption
C.
command injection
D.
blind SQL injection
blind SQL injection
Which system monitors local system operation and local network access for violations of a
security policy?
A.
host-based intrusion detection
B.
systems-based sandboxing
C.
host-based firewall
D.
antivirus
host-based firewall
| Page 9 out of 41 Pages |
| Previous |