Topic 1: Exam Pool A
A help desk technician is troubleshooting a workstation in a SOHO environment that is running above normal system baselines. The technician discovers an unknown executable with a random string name running on the system. The technician terminates the process, and the system returns to normal operation. The technician thinks the issue was an infected file, but the antivirus is not detecting a threat. The technician is concerned other machines may be infected with this unknown virus. Which of the following is the MOST effective way to check other machines on the network for this unknown threat?
A. Run a startup script that removes files by name.
B. Provide a sample to the antivirus vendor
C. Manually check each machine.
D. Monitor outbound network traffic.
Explanation:
The most effective way to check other machines on the network for this unknown threat is
to manually check each machine. This can help to identify any other machines that may be
infected with the unknown virus and allow them to be cleaned.
When a user is in the office, the user's mobile phone loads applications and web browses very slowly on a cellular connection. Which of the following is the best way to fix this issue? Connect to the company's Wi-Fi network.
A. Change the settings on the phone to connect to a different cellular tower.
B. Install a cellular repeater at the office for this user.
C. Update all applications on the phone.
A user's smartphone data usage is well above average. The user suspects an installed application is transmitting data in the background. The user would like to be alerted when an application attempts to communicate with the internet. Which of the following BEST addresses the user's concern?
A. Operating system updates
B. Remote wipe
C. Antivirus
D. Firewall
Explanation:
A firewall is a security system that monitors and controls incoming and outgoing network
traffic based on predetermined security rules. In this scenario, the user is concerned about
an installed application transmitting data in the background, so a firewall would be the best
solution to address their concern. By installing and configuring a firewall, the user can block
unauthorized connections to and from the device, and receive alerts whenever an
application tries to access the internet.
A remote user's smartphone is performing very slowly. The user notices that the performance improves slightly after rebooting but then reverts back to performing slowly. The user also notices that the phone does not get any faster after connecting to the company's corporate guest network. A technician sees that the phone has a large number of applications installed on it. Which of the following is the most likely cause of the issue?
A. The user is in a poor signal area.
B. The user has too many processes running.
C. The smartphone has malware on it.
D. The smartphone has been jailbroken.
A user reports that the hard drive activity light on a Windows 10 desktop computer has been steadily lit for more than an hour, and performance is severely degraded. Which of the following tabs in Task Manager would contain the information a technician would use to identify the cause of this issue?
A. Services
B. Processes
C. Performance
D. Startup
Explanation:
Processes tab in Task Manager would contain the information a technician would use to
identify the cause of this issue. The Processes tab in Task Manager displays all the
processes running on the computer, including the CPU and memory usage of each
process. The technician can use this tab to identify the process that is causing the hard
drive activity light to remain lit and the performance degradation1.
A branch office suspects a machine contains ransomware. Which of the following mitigation steps should a technician take first?
A. Disable System Restore.
B. Remediate the system.
C. Educate the system user.
D. Quarantine the system.
When visiting a particular website, a user receives a message stating, "Your connection is not private." Which of the following describes this issue?
A. Certificate warning
B. Malware
C. JavaScript error
D. Missing OS update
Explanation: A certificate warning is a message that appears when a web browser cannot verify the identity or security of a website. It usually means that there is a problem with the website’s SSL certificate, such as expiration, invalidity, or mismatch. A certificate warning can indicate that the website is unsafe or compromised, and that the user’s connection is not private123.
An executive has contacted you through the help-desk chat support about an issue with a
mobile device.
Assist the executive to help resolve the issue.
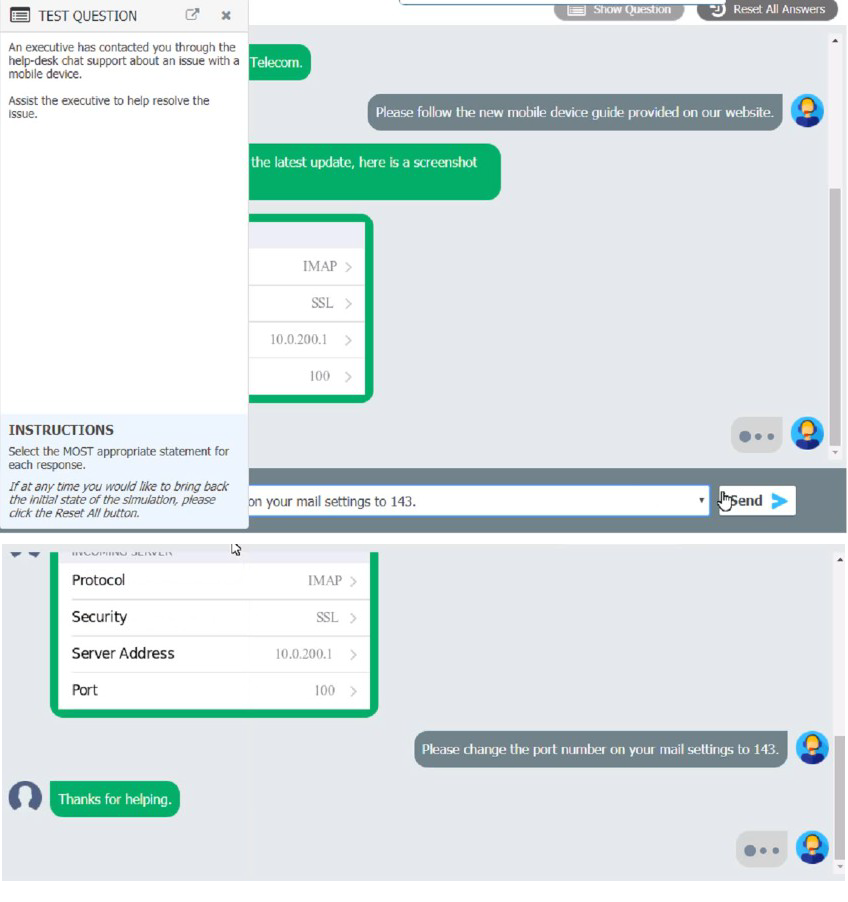
Which of the following should be done NEXT?
A. Educate the user on the solution that was performed.
B. Tell the user to take time to fix it themselves next time.
C. Close the ticket out
D. Send an email to Telecom to inform them of the Issue and prevent reoccurrence
A user's iPhone was permanently locked after several failed log-in attempts. Which of the following authentication methods are needed to restore access, applications, and data to the device?
A. Fingerprint and pattern
B. Facial recognition and PIN code
C. Primary account and password
D. Recovery contact and recovery key
Explanation: If a user’s iPhone is permanently locked after several failed log-in attempts, the user will need to use the recovery contact and recovery key to restore access, applications, and data to the device. The recovery contact is a trusted person who can receive a verification code from Apple and share it with the user. The recovery key is a 28-character code that the user created when setting up two-factor authentication for their Apple ID. The user will need to enter both the verification code and the recovery key on another device or computer to unlock their iPhone. This method will erase the iPhone and restore it from the iCloud backup
A technician installed a known-good, compatible motherboard on a new laptop. However, the motherboard is not working on the laptop. Which of the following should the technician MOST likely have done to prevent damage?
A. Removed all jewelry
B. Completed an inventory of tools before use
C. Practiced electrical fire safety
D. Connected a proper ESD strap
Explanation:
The technician should have connected a proper ESD strap to prevent damage to the
motherboard. ESD (electrostatic discharge) can cause damage to electronic components,
and an ESD strap helps to prevent this by grounding the technician and preventing the
buildup of static electricity. Removing all jewelry is also a good practice, but it is not the
most likely solution to this problem.
| Page 14 out of 74 Pages |
| Previous |