Topic 1: Exam Pool A
Which of the following must be maintained throughout the forensic evidence life cycle when dealing with a piece of evidence?
A. Acceptable use
B. Chain of custody
C. Security policy
D. Information management
Explanation:
The aspect of forensic evidence life cycle that must be maintained when dealing with a
piece of evidence is chain of custody. This is because chain of custody is the
documentation of the movement of evidence from the time it is collected to the time it is
presented in court, and it is important to maintain the integrity of the evidence.
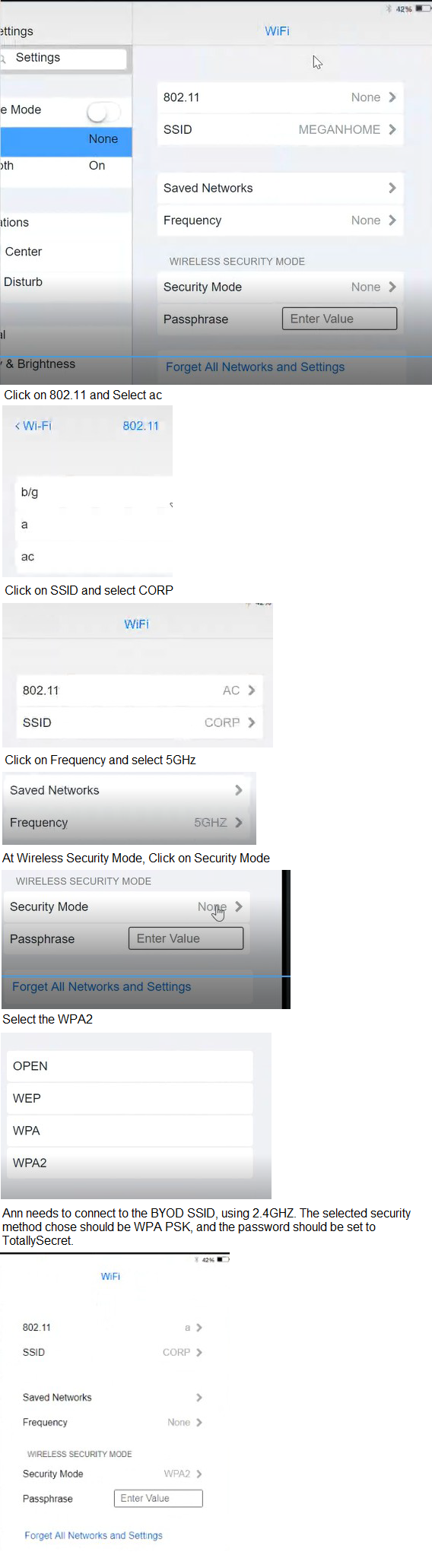
Ann, a CEO, has purchased a new consumer-class tablet for personal use, but she is
unable to connect it to the company’s wireless network. All the corporate laptops are
connecting without issue. She has asked you to assist with getting the device online.
A technician suspects a rootkit has been installed and needs to be removed. Which of the following would BEST resolve the issue?
A. Application updates
B. Anti-malware software
C. OS reinstallation
D. File restore
Explanation:
If a rootkit has caused a deep infection, then the only way to remove the rootkit is to
reinstall the operating system. This is because rootkits are designed to be difficult to detect
and remove, and they can hide in the operating system’s kernel, making it difficult to
remove them without reinstalling the operating system.
A customer service representative is unable to send jobs to a printer at a remote branch office. However, the representative can print successfully to a local network printer. Which of the following commands should a technician use to view the path of the network traffic from the PC?
A. netstat
B. ping
C. format
D. tracert
Explanation: The "tracert" command is used to view the path that network traffic takes from a PC to a specified destination. It is helpful in identifying where along the path the traffic may be failing or experiencing delays. In the scenario where a customer service representative can't send jobs to a remote printer but can print locally, "tracert" can help diagnose if there's a network routing issue affecting the connection to the remote branch office.
A user corrects a laptop that is running Windows 10 to a docking station with external monitors when working at a desk. The user would like to close the laptop when it is docked, but the user reports it goes to sleep when it is closed. Which of the following is the BEST solution to prevent the laptop from going to sleep when it is closed and on the docking station?
A. Within the Power Options of the Control Panel utility click the Change Plan Settings button for the enabled power plan and select Put the Computer to Sleep under the Plugged In category to Never
B. Within the Power Options of the Control Panel utility, click the Change Plan Settings button for the enabled power plan and select Put the Computer to Sleep under the On Battery category to Never
C. Within the Power Options of the Control Panel utility select the option Choose When to Turn Off the Display and select Turn Off the Display under the Plugged In category to Never
D. Within the Power Options of the Control Panel utility, select the option Choose What Closing the Lid Does and select When I Close the Lid under the Plugged in category to Do Nothing
Explanation:
The laptop has an additional option under power and sleep settings that desktops do not
have. Switching to do nothing prevents the screen from turning off when closed.
A technician is troubleshooting a PC that is unable to perform DNS lookups. Utilizing the following firewall output:
Protocol/PortActionDirection 1 AllowOut
445 BlockOut
53 BlockOut
123 BlockOut
80 BlockOut
Which of the following ports should be opened to allow for DNS recursion?
A. 1
B. 53
C. 80
D. 123
E. 445
Which of the following Wi-Fi protocols is the MOST secure?
A. WPA3
B. WPA-AES
C. WEP
D. WPA-TKIP
Which of the following language types enables the automation of tasks?
A. Compiled
B. Scripting
C. Web
D. Database
Explanation: Scripting languages are designed for automating tasks by writing scripts that can execute a series of commands. They are typically easier to write and understand compared to compiled languages and are widely used for automating repetitive tasks, making them the best option for task automation.
A user calls the help desk to report that none of the files on a PC will open. The user also indicates a program on the desktop is requesting payment in exchange for file access A technician verifies the user's PC is infected with ransorrrware. Which of the following should the technician do FIRST?
A. Scan and remove the malware
B. Schedule automated malware scans
C. Quarantine the system
D. Disable System Restore
Explanation:
The technician should quarantine the system first.
Reference:
CompTIA A+ Certification Exam: Core 2 Objectives Version 4.0. Retrieved from
https://partners.comptia.org/docs/default-source/resources/comptia-a-220-1102-examobjectives-(
3-0)
A technician needs to format a USB drive to transfer 20GB of data from a Linux computer to a Windows computer. Which of the following filesystems will the technician MOST likely use?
A. FAT32
B. ext4
C. NTFS
D. exFAT
Explanation:
exFAT is a file system that is supported by both Linux and Windows and can handle large
files1.
| Page 21 out of 74 Pages |
| Previous |