Topic 1: Exam Pool A
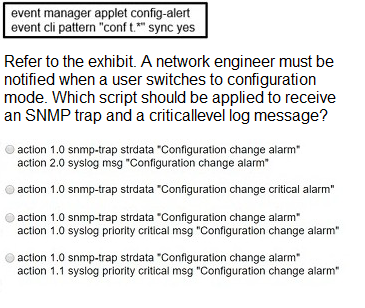
A. Option A
B. Option B
C. Option C
D. Option D
Which technology is the Cisco SD-Access control plane based on?
A. IS-IS
B. LISP
C. Cisco TrustSec
D. VXLAN
Which two operations are valid for RESTCONF? (Choose two)
A. PULL
B. ADD
C. HEAD
D. REMOVE
E. GET
F. PUSH
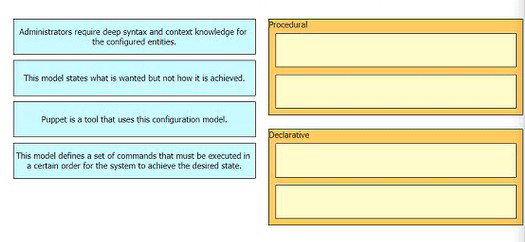
Drag anti drop the characteristics from the ten onto the configuration models on the right.

Which AP mode analyzes the spectrum to detect sources of interference?
A. Monitor
B. Rogue detector
C. SE-Connect
D. Sniffer
With IGMPv2, which multicast group address does the IGMP querier use to send query messages to all hosts on the LAN?
A. 239.0.0.2
B. 224.0.0.1
C. 239.0.0.1
D. 224.0.0.2
Which protocol is used by vmanage to push centralized policies to vsmart controllers?
A. NETCONF
B. TLS
C. STUN
D. OMP
A wireless administrator must create a new web authentication corporate SSID that will be using ISE as the external RADIUS server. The guest VLAN must be specified after the authentication completes. Which action must be performed to allow the ISE server to specify the guest VLAN?
A. Set RADIUS Profiling.
B. Set AAA Policy name.
C. Enable Network Access Control State.
D. Enable AAA Override.
A network administrator is preparing a Python script to configure a Cisco IOS XEbased device on the network. The administrator is worried that colleagues will make changes to the device while the script is running. Which operation of the NC client manager prevents colleagues from making changes to the devices while the script is running?
A. m.freeze(config-running')
B. m.freeze(target-running')
C. m.lock(config='running')
D. m.lock(target-running')
Which message type is valid for IGMPv3?
A. leave group
B. hello
C. graft
D. source-specific membership report
| Page 4 out of 26 Pages |
| Previous |