Topic 1: Exam Pool A
What is used to validate the authenticity of the client and is sent in HTTP requests as a JSON object?
A. SSH
B. TLS
C. HTTPS
D. JWT
A. Option A
B. Option B
C. Option C
D. Option D
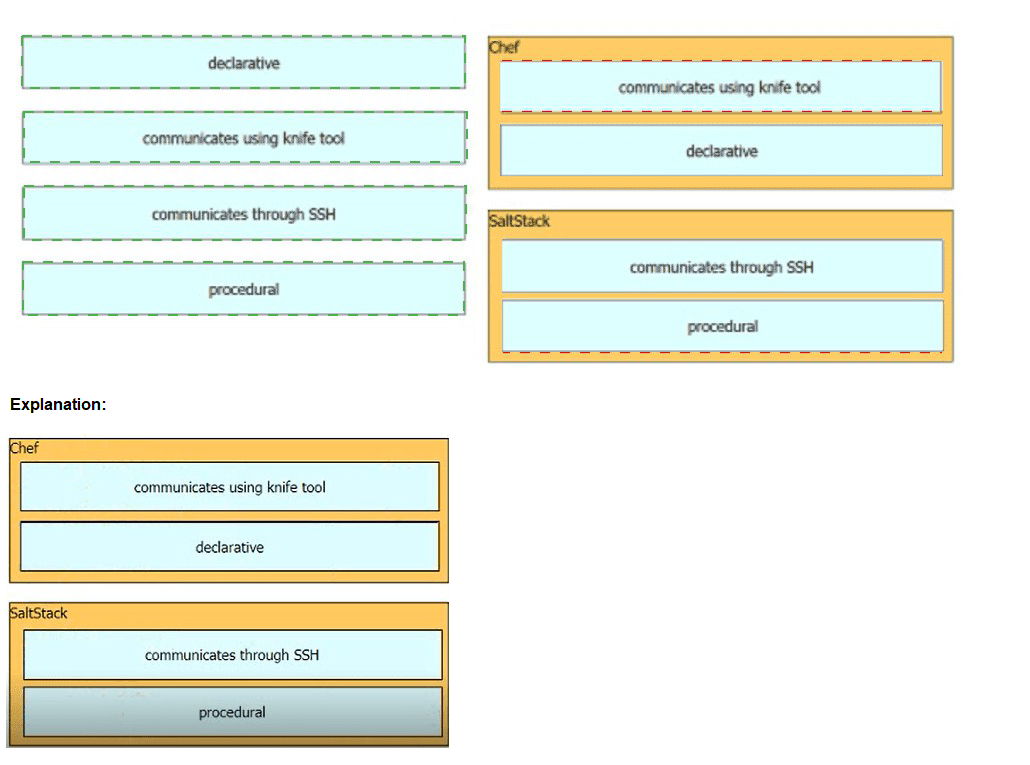
Drag and drop the characteristics from the left into the orchestration tools that they describe on the right.
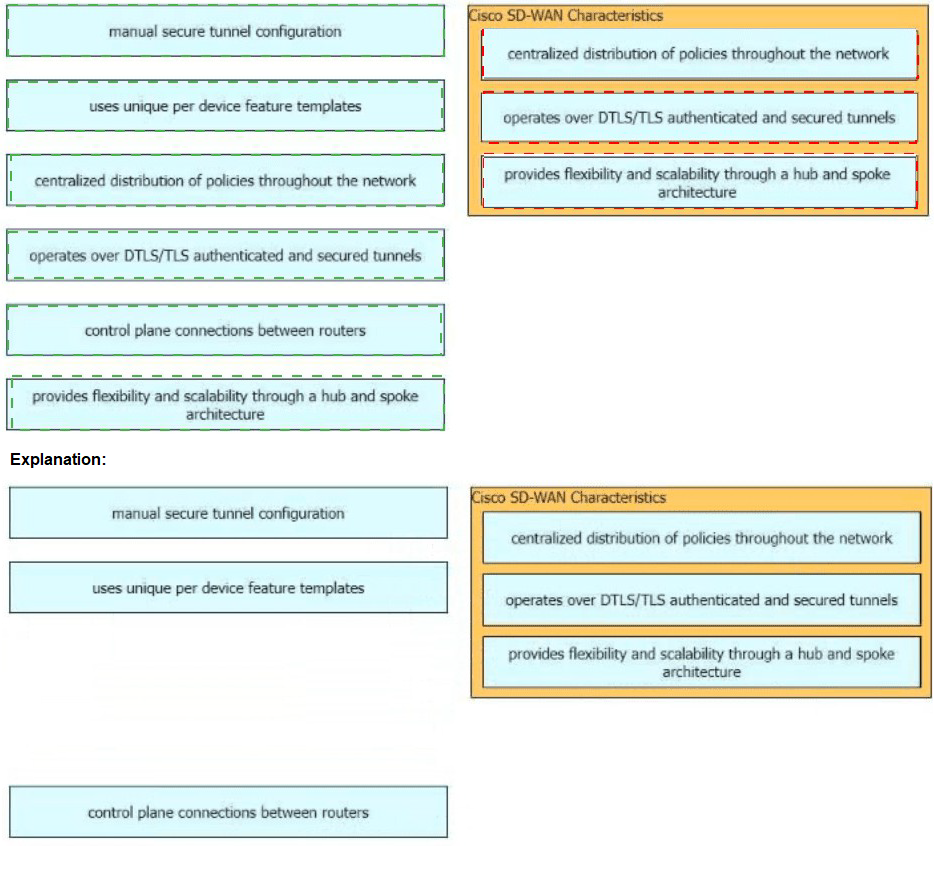
Drag and drop the characteristics of Cisco Catalyst SD-WAN from the left onto the right. Not all options are used.
A response code of 404 is received while using the REST API on Cisco UNA Center to
POST to this URI.
/dna/intent/api/v1 /template-programmer/project
What does the code mean?
A. The client made a request a resource that does not exist.
B. The server has not implemented the functionality that is needed to fulfill the request.
C. The request accepted for processing, but the processing was not completed.
D. The POST/PUT request was fulfilled and a new resource was created, Information about the resource is in the response body.
What is one characteristic of an AP that is operating in Mobility Express mode?
A. It is recommended for large scale deployments.
B. It requires a centralized WLC.
C. At least three APs are needed for WLC redundancy.
D. It requires an AP to act as a WLC.
A customer requests a design that includes GLBP as the FHRP. The network architect discovers that the members of the GLBP group have different throughput capabilities. Which GLBP load balancing method supports this environment?
A. host dependent
B. weighted
C. least connection
D. round robin
What are two methods of ensuring that the multicast RPF check passes without changing the unicast routing table? (Choose two.)
A. disabling the interface of the router back to the multicast source
B. implementing MBGP
C. disabling BGP routing protocol
D. implementing static mroutes
E. implementing OSPF routing protocol
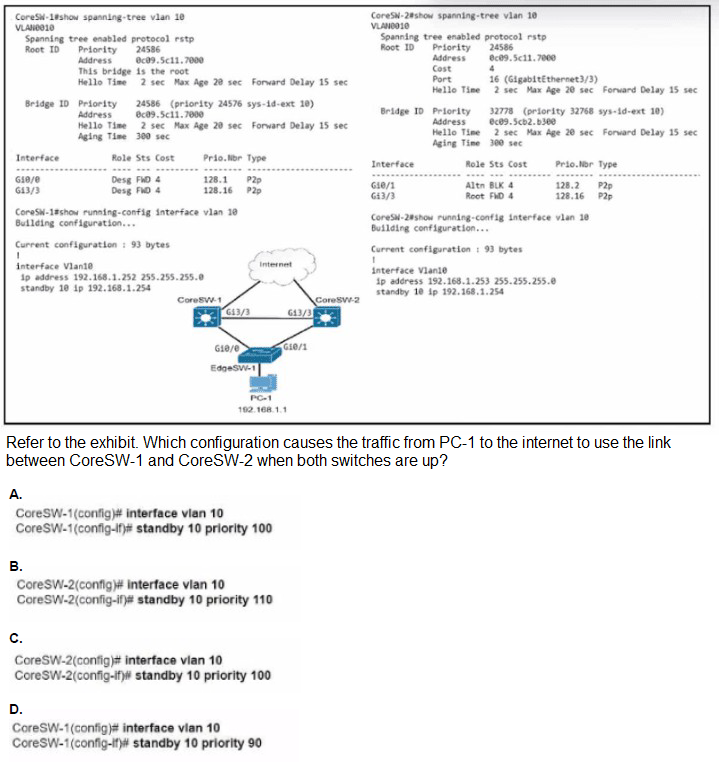
Refer to the exhibit.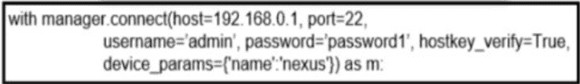
What does the snippet of code achieve?
A. It creates a temporary connection to a Cisco Nexus device and retrieves a token to be used for API calls.
B. It opens a tunnel and encapsulates the login information, if the host key is correct.
C. It opens an ncclient connection to a Cisco Nexus device and maintains it for the duration of the context.
D. It creates an SSH connection using the SSH key that is stored, and the password is ignored.
When deploying Cisco SD-Access Fabric APs, where does the data plane VXLAN tunnel terminate?
A. on the first-hop fabric edge switch
B. on the WLC node
C. on the fabric border node switch
D. directly on the fabric APs
| Page 9 out of 26 Pages |
| Previous |