A company is using IAM Organizations. The company wants to restrict IAM usage to the eu-west-1 Region for all accounts under an OU that is named "development." The solution must persist restrictions to existing and new IAM accounts under the development OU.

A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option A
A company deployed IAM Organizations to help manage its increasing number of IAM accounts. A security engineer wants to ensure only principals in the Organization structure can access a specic Amazon S3 bucket. The solution must also minimize operational overhead. Which solution will meet these requirements?
A.
1 Put all users into an IAM group with an access policy granting access to the J bucket.
B.
Have the account creation trigger an IAM Lambda function that manages the bucket policy, allowing access to accounts listed in the policy only.
C.
Add an SCP to the Organizations master account, allowing all principals access to the bucket.
D.
Specify the organization ID in the global key condition element of a bucket policy, allowing all principals access.
Specify the organization ID in the global key condition element of a bucket policy, allowing all principals access.
A company is using AWS Organizations to manage multiple AWS accounts for its hu-man resources, finance, software development, and production departments. All the company's developers are part of the software development AWS account. The company discovers that developers have launched Amazon EC2 instances that were preconfigured with software that the company has not approved for use. The company wants to implement a solution to ensure that developers can launch EC2 instances with only approved software applications and only in the software de-velopment AWS account. Which solution will meet these requirements?
A.
In the software development account, create AMIS of preconfigured instanc-es that include only approved software. Include the AMI IDs in the condi-tion section of an AWS CloudFormation template to launch the appropriate AMI based on the AWS Region. Provide the developers with the CloudFor-mation template to launch EC2 instances in the software development ac-count.
B.
Create an Amazon EventBridge rule that runs when any EC2 Runlnstances API event occurs in the software development account. Specify AWS Systems Man-ager Run Command as a target of the rule. Configure Run Command to run a script that will install all approved software onto the instances that the developers launch.
C.
Use an AWS Service Catalog portfolio that contains EC2 products with ap-propriate AMIS that include only approved software. Grant the developers permission to portfolio access only the Service Catalog to launch a prod-uct in the software development account.
D.
In the management account, create AMIS of preconfigured instances that in-clude only approved software. Use AWS CloudFormation StackSets to launch the AMIS across any AWS account in the organization. Grant the developers permission to launch the stack sets within the management account.
Use an AWS Service Catalog portfolio that contains EC2 products with ap-propriate AMIS that include only approved software. Grant the developers permission to portfolio access only the Service Catalog to launch a prod-uct in the software development account.
A company is running its workloads in a single AWS Region and uses AWS Organizations. A security engineer must implement a solution to prevent users from launching resources in other Regions. Which solution will meet these requirements with the LEAST operational overhead?
A.
Create an IAM policy that has an aws RequestedRegion condition that allows actions only in the designated Region Attach the policy to all users.
B.
Create an I AM policy that has an aws RequestedRegion condition that denies actions that are not in the designated Region Attach the policy to the AWS account in AWS Organizations.
C.
Create an IAM policy that has an aws RequestedRegion condition that allows the desired actions Attach the policy only to the users who are in the designated Region.
D.
Create an SCP that has an aws RequestedRegion condition that denies actions that are not in the designated Region. Attach the SCP to the AWS account in AWS Organizations.
Create an SCP that has an aws RequestedRegion condition that denies actions that are not in the designated Region. Attach the SCP to the AWS account in AWS Organizations.
Explanation: Although you can use a IAM policy to prevent users launching resources in other regions. The best practice is to use SCP when using AWS organizations.
https://docs.aws.amazon.com/organizations/latest/userguide/orgs_manage_policies_scps_examples_general.html#example-scp-deny-region
A company has an encrypted Amazon Aurora DB cluster in the us-east-1 Region. The DB cluster is encrypted with an AWS Key Management Service (AWS KMS) customer managed key. To meet compliance requirements, the company needs to copy a DB snapshot to the us-west-1 Region. However, when the company tries to copy the snapshot to us-west-1 the company cannot access the key that was used to encrypt the original database. What should the company do to set up the snapshot in us-west-1 with proper encryption?
A.
Use AWS Secrets Manager to store the customer managed key in us-west-1 as a secret Use this secret to encrypt the snapshot in us-west-1.
B.
Create a new customer managed key in us-west-1. Use this new key to encrypt the snapshot in us-west-1.
C.
Create an IAM policy that allows access to the customer managed key in us-east-1. Specify am aws kms us-west-1 " as the principal.
D.
Create an IAM policy that allows access to the customer managed key in us-east-1. Specify arn aws rds us-west-1. * as the principal.
Create a new customer managed key in us-west-1. Use this new key to encrypt the snapshot in us-west-1.
Explanation: "If you copy an encrypted snapshot across Regions, you must specify a KMS key valid in the destination AWS Region. It can be a Region-specific KMS key, or a multi- Region key." https://docs.aws.amazon.com/AmazonRDS/latest/AuroraUserGuide/auroracopy-snapshot.html#aurora-copy-snapshot.Encryption
A company receives a notification from the AWS Abuse team about an AWS account The notification indicates that a resource in the account is compromised The company determines that the compromised resource is an Amazon EC2 instance that hosts a web application The compromised EC2 instance is part of an EC2 Auto Scaling group The EC2 instance accesses Amazon S3 and Amazon DynamoDB resources by using an 1AM access key and secret key The 1AM access key and secret key are stored inside the AMI that is specified in the Auto Scaling group's launch configuration The company is concerned that the credentials that are stored in the AMI might also have been exposed The company must implement a solution that remediates the security concerns without causing downtime for the application The solution must comply with security best practices Which solution will meet these requirements'?
A.
Rotate the potentially compromised access key that the EC2 instance uses Create a new AM I without the potentially compromised credentials Perform an EC2 Auto Scaling instance refresh.
B.
Delete or deactivate the potentially compromised access key Create an EC2 Auto Scaling linked 1AM role that includes a custom policy that matches the potentially
compromised access key permission Associate the new 1AM role with the Auto Scaling group Perform an EC2 Auto Scaling instance refresh.
C.
Delete or deactivate the potentially compromised access key Create a new AMI without the potentially compromised credentials Create an 1AM role that includes the correct permissions Create a launch template for the Auto Scaling group to reference the new AMI and 1AM role Perform an EC2 Auto Scaling instance refresh.
D.
Rotate the potentially compromised access key Create a new AMI without the potentially compromised access key Use a user data script to supply the new access key as environmental variables in the Auto Scaling group's launch configuration Perform an EC2 Auto Scaling instance refresh.
Delete or deactivate the potentially compromised access key Create a new AMI without the potentially compromised credentials Create an 1AM role that includes the correct permissions Create a launch template for the Auto Scaling group to reference the new AMI and 1AM role Perform an EC2 Auto Scaling instance refresh.
A company accidentally deleted the private key for an Amazon Elastic Block Store (Amazon EBS)-backed Amazon EC2 instance. A security engineer needs to regain access to the instance. Which combination of steps will meet this requirement? (Choose two.)
A.
Stop the instance. Detach the root volume. Generate a new key pair.
B.
Keep the instance running. Detach the root volume. Generate a new key pair.
C.
When the volume is detached from the original instance, attach the volume to another instance as a data volume. Modify the authorized_keys file with a new public key. Move the volume back to the original instance. Start the instance.
D.
When the volume is detached from the original instance, attach the volume to another instance as a data volume. Modify the authorized_keys file with a new private key. Move the volume back to the original instance. Start the instance.
E.
When the volume is detached from the original instance, attach the volume to another instance as a data volume. Modify the authorized_keys file with a new public key. Move the volume back to the original instance that is running.
Stop the instance. Detach the root volume. Generate a new key pair.
When the volume is detached from the original instance, attach the volume to another instance as a data volume. Modify the authorized_keys file with a new public key. Move the volume back to the original instance. Start the instance.
Explanation:
If you lose the private key for an EBS-backed instance, you can regain access to your instance. You must stop the instance, detach its root volume and attach it to another instance as a data volume, modify the authorized_keys file with a new public key, move the volume back to the original instance, and restart the instance.
https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/TroubleshootingInstancesConnecting.html#replacing-lost-key-pai
A company is using IAM Organizations to develop a multi-account secure networking strategy. The company plans to use separate centrally managed accounts for shared services, auditing, and security inspection. The company plans to provide dozens of additional accounts to application owners for production and development environments. Company security policy requires that all internet traffic be routed through a centrally managed security inspection layer in the security inspection account. A security engineer must recommend a solution that minimizes administrative overhead and complexity. Which solution meets these requirements?
A.
Use IAM Control Tower. Modify the default Account Factory networking template to automatically associate new accounts with a centrally managed VPC through a VPC peering connection and to create a default route to the VPC peer in the default route table. Create an SCP that denies the CreatelnternetGateway action. Attach the SCP to all accounts except the security inspection account.
B.
Create a centrally managed VPC in the security inspection account. Establish VPC peering connections between the security inspection account and other accounts. Instruct account owners to create default routes in their account route tables that point to the VPC peer. Create an SCP that denies the Attach InternetGateway action. Attach the SCP to all accounts except the security inspection account.
C.
Use IAM Control Tower. Modify the default Account Factory networking template to automatically associate new accounts with a centrally managed transit gateway and to create a default route to the transit gateway in the default route table. Create an SCP that denies the AttachlnternetGateway action. Attach the SCP to all accounts except the security inspection account.
D.
Enable IAM Resource Access Manager (IAM RAM) for IAM Organizations. Create a shared transit gateway, and make it available by using an IAM RAM resource share. Create an SCP that denies the CreatelnternetGateway action. Attach the SCP to all accounts except the security inspection account. Create routes in the route tables of all accounts that point to the shared transit gateway.
Use IAM Control Tower. Modify the default Account Factory networking template to automatically associate new accounts with a centrally managed transit gateway and to create a default route to the transit gateway in the default route table. Create an SCP that denies the AttachlnternetGateway action. Attach the SCP to all accounts except the security inspection account.
A company created an IAM account for its developers to use for testing and learning purposes Because MM account will be shared among multiple teams of developers, the company wants to restrict the ability to stop and terminate Amazon EC2 instances so that a team can perform these actions only on the instances it owns.
Developers were Instructed to tag al their instances with a Team tag key and use the team name in the tag value One of the first teams to use this account is Business Intelligence A security engineer needs to develop a highly scalable solution for providing developers with access to the appropriate resources within the account The security engineer has already created individual IAM roles for each team.
Which additional configuration steps should the security engineer take to complete the task?
A. For each team, create an AM policy similar to the one that fellows Populate the ec2:
ResourceTag/Team condition key with a proper team name Attach resulting policies to the corresponding IAM roles.
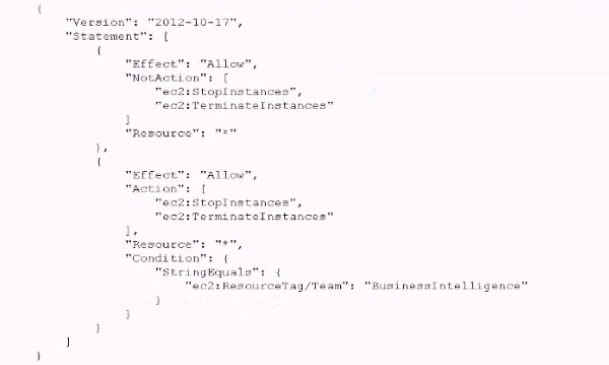
B. For each team create an IAM policy similar to the one that follows Populate the IAM TagKeys/Team condition key with a proper team name. Attach the resuming policies to the corresponding IAM roles.

C. Tag each IAM role with a Team lag key. and use the team name in the tag value. Create an IAM policy similar to the one that follows, and attach 4 to all the IAM roles used by developers.
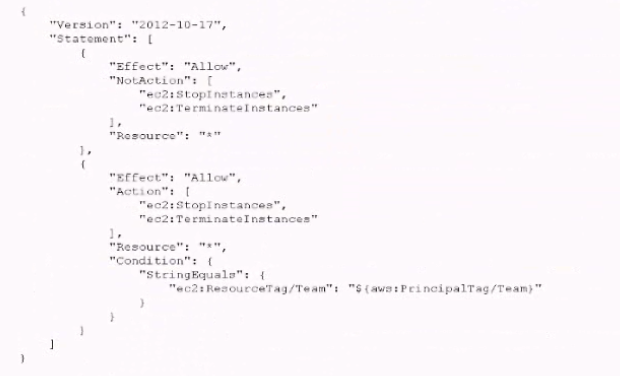
D. Tag each IAM role with the Team key, and use the team name in the tag value. Create an IAM policy similar to the one that follows, and it to all the IAM roles used by developers.


A company hosts business-critical applications on Amazon EC2 instances in a VPC. The VPC uses default DHCP options sets. A security engineer needs to log all DNS queries that internal resources make in the VPC. The security engineer also must create a list of the most common DNS queries over time. Which solution will meet these requirements?
A.
Install the Amazon CloudWatch agent on each EC2 instance in the VPC. Use the CloudWatch agent to stream the DNS query logs to an Amazon CloudWatch Logs log group. Use CloudWatch metric filters to automatically generate metrics that list the most common ONS queries.
B.
Install a BIND DNS server in the VPC. Create a bash script to list the DNS request number of common DNS queries from the BIND logs.
C.
Create VPC flow logs for all subnets in the VPC. Stream the flow logs to an Amazon CloudWatch Logs log group. Use CloudWatch Logs Insights to list the most common DNS queries for the log group in a custom dashboard.
D.
Configure Amazon Route 53 Resolver query logging. Add an Amazon CloudWatch Logs log group as the destination. Use Amazon CloudWatch Contributor Insights to analyze the data and create time series that display the most common DNS queries.
Configure Amazon Route 53 Resolver query logging. Add an Amazon CloudWatch Logs log group as the destination. Use Amazon CloudWatch Contributor Insights to analyze the data and create time series that display the most common DNS queries.
Explanation: https://aws.amazon.com/blogs/aws/log-your-vpc-dns-queries-with-route-53-resolver-query-logs/
| Page 11 out of 37 Pages |
| Previous |